Executive Summary
Ransomeware-as-a-service (RaaS) has become popular because of its ease of use, even by non-technical criminals, in addition to its low membership fee for its return on investment. Most frighteningly, it opens up the option of conducting ransomeware attacks to criminals without extensive technical know-how.
In this article we explore Ransomeware-as-a-service in more detail: what it is, how it works, its features, the most popular RaaS tools in use, and how organisations can protect themselves.
What is RaaS?
Since the emergence of cloud computing, software is now drifting away from locally installed applications to Software-as-a-Service web applications facilitated by remote servers. This trend has provided opportunities to cyber criminals to cash in on this trend, which has led to the creation of Ransomware-as-a-Service (RaaS). RaaS provides cybercriminals with access to a ransomware. It is then distributed through signing up to the service where the service provider offers ransomware and a payment server. The member will distribute the ransomware to infect victims and get ransom payments from them. The payment amount is then shared by the member and the service provider. In 2015, Tox became the first RaaS. The criminals behind Tox created a malware in which once opened on a windows operating system, encrypts all files. The malware was available via the well-known ‘dark net’ TOR. Since then, there have been many that have emerged including Encrypter, Satan, Yatron, Petya, Jokeroo and Cryptolocker Service.
How does it work?
RaaS creators host their ransomware on a darknet onion site whereby cybercriminals can purchase the ransomware at a subscription price. The price varies depending on the features offered. A free subscription is also available up to certain basic features. However, affiliates need to become a member of the RaaS by paying an initial deposit. Once members use the ransomware to infect computers and get ransom payments from victims, the amount is shared with the service provider at an agreed proportion.
Adverts for RaaS are widely shared on TOR – see below for a screenshot example of a Satan Ransomeware advert.
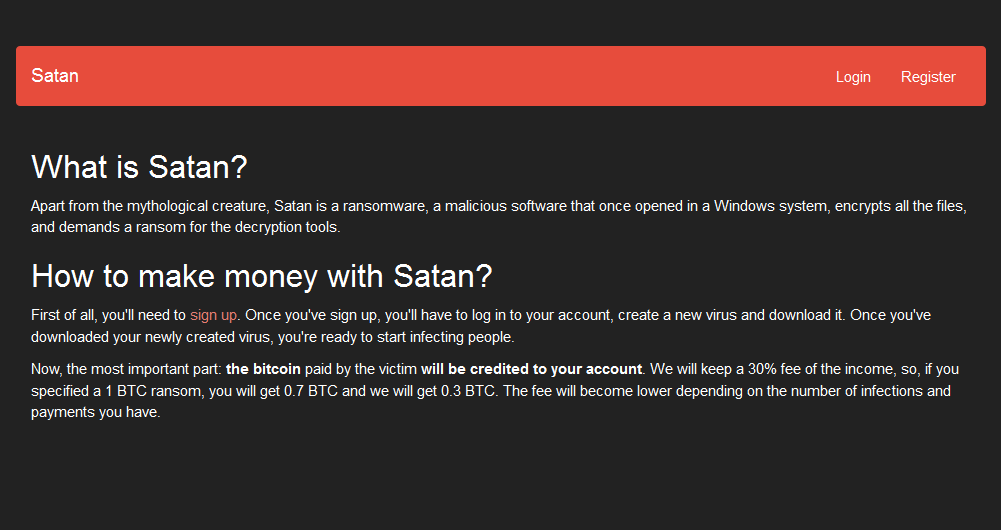
Source: TOR
RaaS Features
Various features are offered depending on the membership packages chosen by the affiliate. These include, but not limited to:
- Generating your own ransom notes, logo design and extension
- Infecting an unlimited number of victims
- Encrypting all discs and files and deleting shadow copy
- Multiple choices of payment cryptocurrency options
List of Popular RaaS
- Satan RaaS was offered for free, however, affiliates have to sign up to the RaaS by paying an initial payment. The Satan platform allows inexperienced cybercriminals to execute large scale ransomware attacks through their guidelines to malware distribution.
- Yatron RaaS was promoted via Twitter that planned on using the EternalBlue and DoublePulsar exploits to distribute to other systems on a network. The RaaS is offered for a single payment of $100. Yatron RaaS offers Fully Undetectable (FUD) ransomware and FUD decryptor with the ability to spread via P2P, USB, and LAN.
- Jokeroo RaaS was involved in an exit scam whereby the TOR site hosting the RaaS displayed a notice which stated that their servers was seized by the authorities. Jokeroo RaaS was where affiliates could buy multiple membership packages ranging from $90 to $600. Jokeroo never achieved wide distribution, but samples were spotted in the wild.
Conclusion
Conventional Anti-virus (AV) software can only work to protect against threats they know. This means businesses behind AV must identify and analyse the threat beforehand to adapt their protection. Unfortunately, the only way this is achieved is if someone gets infected first and reports it. Nowadays, cybercriminals often create new variants of the same ransomware with a new campaign.
RaaS opens up ransomeware potential to a new breed of (less technically-minded) criminal. Given the growing threat, it is ever more imperative businesses adequately protect themselves against ransomeware attacks. There are four simple things every business should do:
- Making regular backups
- Paying attention and discard emails with suspicious attachments or extensions
- Keeping all systems and software updated
- Creating a cyber security culture
Learn more about QA’s cyber security training solutions.
More articles by James
The Air-Gap Dilemma
QA Cyber Security Specialist, James Aguilan, looks at the methods through which air-gapped systems can be compromised.
26 March 2019Safeguarding your Digital Footprint
QA Cyber Security Trainer, James Aguilan, shares 6 tips that can help you safeguard your digital footprint.
05 March 2018Phishing Campaigns: Defending organisations against phishing
QA Cyber Security Trainer, James Aguilan, argues that understanding how to defend against phishing is of paramount importance for the confidentiality and integrity o…
15 February 2018Most common ways for thieves to steal your cryptocurrency
QA Cyber Security Trainer, James Aguilan, looks at how cybercriminals can steal your coins.
19 July 2018Is Mr Robot a good representation of real-life hacking and hacking culture?
QA Cybersecurity trainer James Aguilan looks at several scenarios featured in the hit US TV series Mr Robot – and how they may represent real-life hacking.
19 February 2018How to build an effective cyber defence against polymorphic malware
QA Cyber Security Trainer, James Aguilan, lists three key areas where security efforts should be focussed to counter polymorphic malware.
11 October 2018How do organisations demonstrate accountability for GDPR compliance?
QA Cyber Security Trainer, James Aguilan, outlines steps towards demonstrating compliance with the GDPR.
20 March 2018Cyber criminals can exploit flaws in online security and all new appliances
QA Cyber Security Trainer, James Aguilan, looks at how internet-enabled devices such as fridges, doorbells and TVs are leaving consumers exposed to hackers.
22 May 2018Cryptocurrency Mining: Does the reward outweigh the cost?
QA Cyber Security Trainer, James Aguilan, looks at the practice of mining cryptocurrency.
27 March 2018Cryptocurrency in traditional crimes
QA Cyber Security Trainer, James Aguilan, looks at how cryptocurrency is used in crimes such as drug trafficking, money laundering and fraud.
25 July 2018
