Top 10 Cyber Certifications of 2026
According to the World Economic Forum (WEF) over 90% of security leaders will pay for employee to complete security certifications. Global shortage of skills, job movers and growing cyber threats drives demand for security skills certifications for the foreseeable future.
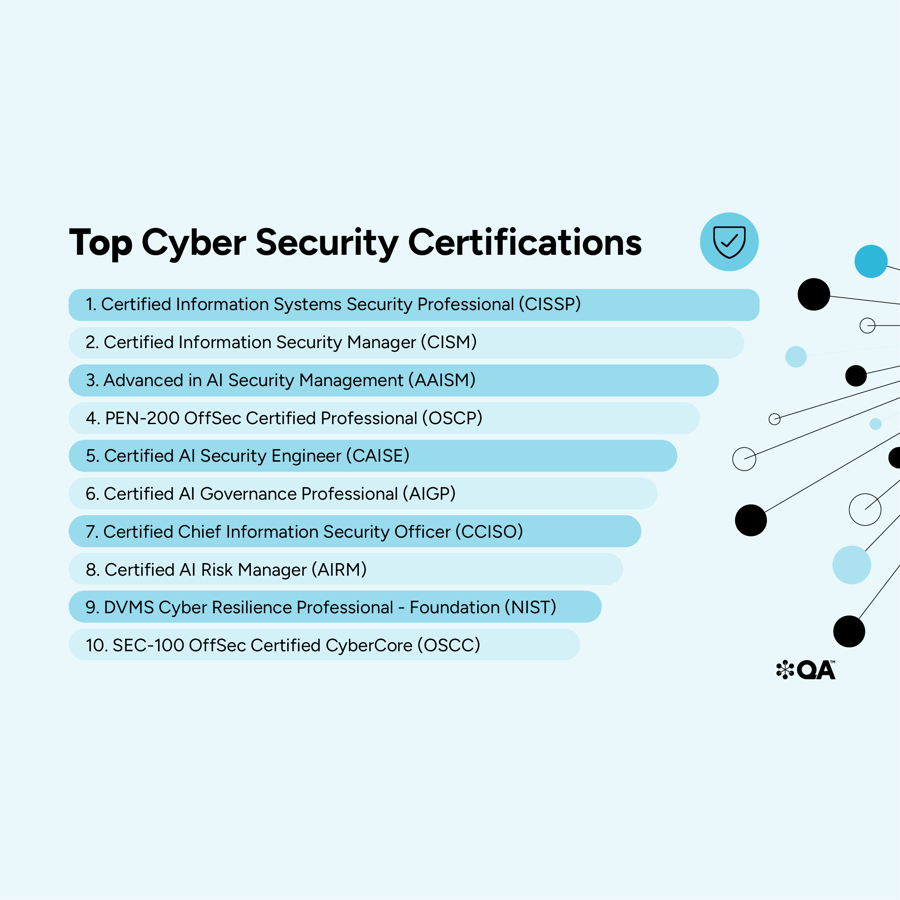
Demand for cyber security professionals is at an all time high, making cyber security certifications a valuable asset for professionals that want to advance their career and validate their skills. To help you decide on your next cyber qualification, QA's Portfolio Director for Cyber Security, Richard Beck, has selected his Top 10 cyber security certifications for 2026.
Richard Beck is an experienced security professional, turned educator, with over 15 years in operational security roles.
1. Certified Information Systems Security Professional (CISSP)

The ISC2 Certified Information Systems Security Professional (CISSP) certification is the gold standard in cyber security certifications. If you’re looking to establish credibility in the field or elevate your expertise, CISSP can be a career defining achievement.
Who is CISSP best for?
- Security Managers
- Security Consultants
- IT Directors
- Security Architects
- Network Architects.
Prerequisites
CISSP is intended for professionals who have at least five years of cumulative, paid work experience in two or more of the eight domains of the (ISC)²® CISSP CBK and are pursuing CISSP training and certification to advance within their current information security careers.
Learn more about CISSP, or book a CISSP training course with our experts today.
2. Certified Information Security Manager (CISM)
Enterprises and government agencies increasingly expect their IT professionals to hold a CISM certification, and it is considered essential to ongoing education and career development. ISACA's CISM certification gives you the skills to build and lead security programs, aligning global best practices with evolving enterprise needs.
Who is CISM For?
- Security Consultants
- IT Directors
- Security Auditors and Architects
- Security Systems Engineers
- Chief Information Security Officers (CISOs)
- Chief Compliance/Privacy/Risk Officers
Prerequisites
Although the examination is open to all individuals who have an interest in information security, a minimum of 5 years of professional information systems auditing, control or security work experience is required for the CISM certification.
Learn more about CISM, or book a CISM course with our experts.
3. Advanced in AI Security Management (AAISM)

The ISACA Advanced in AI Security Management (AAISM™) from ISACA certification equips security leaders with the knowledge and capability to govern, secure, and manage enterprise AI systems.
Who is OSCP For?
- Experience cyber security managers
- Governance, risk and compliance professionals
- Cyber teams working in enterprise environments
Prerequisites
Before taking this course, you should a CISM or CISSP certification and proven experience in security or consultancy roles. You should also have a foundational understanding of AI systems.
Book Advanced in AI Security Management
4. PEN-200 OffSec Certified Professional (OSCP)
The OSCP certification from Offsec is considered to be more technical than other ethical hacking certifications and is one of the few that requires evidence of practical penetration testing skills.
It is a lifetime certification and considered one of the best pen testing certifications due to it's tough test, which requires holders to successfully attack and penetrate various live machines in a safe lab environment.
Who is OSCP For?
- Infosec professionals transitioning into pen testing
- Penetration testers seeking the best penetration testing certifications
- Security professionals
- Network administrators
Prerequisites
Exam takers need to have completed the PEN-200 courses to be eligible for OSCP, and should have reasonable experience in Windows and Linux Administration, basic Bash and/or Python scripting and TC/IP networking.
Learn more about OSCP, or book an OSCP course with our experts today.
5. Certified AI Security Engineer (CAISE)
Discover how to securely integrate LLMs into your applications, safeguard training data, build robust AI infrastructure, and ensure effective human-AI interaction. By the end of this course, you'll be equipped to protect your organization's AI assets and maintain the integrity of your systems.
Who is CAISE For?
- Cyber Security Professionals
- AI & ML Tech Specialists
- Risk Managers
- AI Governance Professionals
- Data Architects
- Technical Consultants
- IT Professionals
- Software Engineers.
Prerequisites
No prerequisites, aside general understanding of AI principles.
Learn more about CAISE, or book a CAISE Certification Course
6. Certified AI Governance Professional (AIGP)

With the expansion of AI technology, there is a need for professionals in all industries to understand and execute responsible AI governance. The AIGP credential demonstrates that an individual can ensure safety and trust in the development and deployment of ethical AI and ongoing management of AI systems.
Who is AIGP For?
- Compliance Managers
- Privacy Professionals
- Security Risk Managers
- HR & Governance Teams
- Data Scientists
- AI Project Managers & Owners
Prerequisites
There are no prerequisites for this course.
Learn more about AIGP or book an AI GP course
7. Certified Chief Information Security Officer
Designed by industry experts, the Certified Chief Security Information Security Officer certification from EC-Council equips aspiring CISOs with the strategic, technical, and leadership skills needed to build and manage world-class security programs.
Each segment of the program was developed with the aspiring CISO in mind and looks to transfer the knowledge of seasoned professionals to the next generation in the areas that are most critical in the development and maintenance of a successful information security program.
Who is CCISO For?
- Security Management Roles
- Individuals with a CISSP, CISM or CISA qualification already
Prerequisites
Candidates interested in earning the C|CISO Certification must qualify via ECCouncil’s Exam Eligibility application before booking the C|CISO course
Learn more about CCISO or Book a CCISO Course
8. Certified AI Risk Manager (AIRM)
This course equips professionals with the knowledge and tools to identify, assess, and mitigate AI-related risks within modern organisations. It explores the principles of AI governance, compliance, and ethics through globally recognised frameworks such as the NIST AI Risk Management Framework and the EU AI Act
Who is AIRM For?
This course is best suited for those in AI-adjacent roles, giving AI developers and engineers the knowledge they need in governance, risk and compliance protocols.
Prerequisites
Learners should have a basic understand of AI concepts and data governance principles, as well as knowledge of organisational risk management and information security practices.
Book Certified AI Risk Manager
9. DVMS Cyber Resilience Professional - Foundation
This foundation-level course provides IT service management, governance, risk, compliance, and cybersecurity professionals with an in-depth understanding of the NIST Cybersecurity Framework (NIST-CSF) and its integration within a Digital Value Management System (DVMS). Participants explore how NIST-CSF supports the creation of an adaptive, integrated, and culture-driven governance and assurance system capable of delivering resilient, compliant, and trusted digital outcomes.
Who is DVMS Cyber Resilience Professional - Foundation For?
- IT service management professionals responsible for digital governance and compliance.
- Cybersecurity and risk management professionals aiming to integrate NIST-CSF into organisational practices.
- Business leaders, consultants, and assurance specialists responsible for achieving resilient and trusted digital outcomes.
- Teams or departments implementing adaptive governance and assurance models within a DVMS.
Prerequisites
There are no formal prerequisites for this course. It is suitable for professionals involved in designing, implementing, operating, or improving digital governance and assurance systems that deliver secure and compliant outcomes.
Book a DVMS Cyber Resilience Professional - Foundation Course
10. SEC-100 OffSec Certified CyberCore (OSCC)
SEC-100 Security Essentials provides a comprehensive foundation in cybersecurity for learners at the beginning of their careers. Covering a breadth of essential topics across governance and risk frameworks, offensive, defensive, and secure-by-design disciplines.
Who is OSIR For?
This certification is best suited to those who are just embarking on a career in cyber security.
Prerequisites
There are no prerequisites for this course, other than basic digital literacy and willingness to learn more.
Book a SEC-100 Course
Cyber certifications by job role
Best entry level cyber certifications
Just getting started in cyber security? These are the best qualifications you can earn to kickstart your career:
CompTIA Security+
The CompTIA Security+ five day course is designed to help you prepare for the SY0-701 exam, which is included in your course. This is the ideal course for those looking to kickstart a career in cyber security.
Certificate in Information Security Management Principles (CISMP)
CISMP is a practical NCSC Assured course designed to provide the knowledge and skills required to manage information security, information assurance or information risk based processes.
Aligned with the latest national information assurance frameworks, standards, and code of practice for information security.
Best for cloud security
If you work as a cloud security engineer, or want to specialise in cloud operations in the future, these are two of the best certifications you can earn:
Practitioner Certification in Cloud Security
This NCSC Assured hands-on vendor agnostic course, encompassing cloud security architecture, cloud security testing, identity & access management, DevSecOps, cloud data security, cloud assurance, governance, cloud security operations, web application security, and Zero Trust in the cloud and cloud supply chain.
Certified Cloud Security Professional
The CCSP is a cloud agnostic course ensures that cloud security professionals have the required knowledge, skills, and abilities in cloud security design, multi-cloud, implementation, architecture, operations, service orchestration, controls, and compliance with regulatory frameworks.
This professional competence is measured against a globally recognised body of knowledge.
Best for software security professionals
Those who specialise in software security need the skills to protect applications at every stage of the development cycle.
Secure by Design
Master the art of secure software development by exploring industry-leading models, threat modeling techniques, and cutting-edge security best practices. From AI-generated code challenges to the latest OWASP vulnerabilities, this course equips you with the knowledge and tools to build resilient, secure-by-design applications.
Certified Secure Software Lifecycle Professional
The CSSLP is a comprehensive review of the knowledge required to incorporate security practices, including authentication, authorisation and auditing, into each phase of the Software Development Lifecycle, from software design and implementation to testing and deployment. Content aligns with and comprehensively covers the eight domains of the body of knowledge.
Best for security architecture
Learn how to manage threats and develop security architecture with these specialist certifications.
Hands-On Threat Modelling Certificate
Hands-on threat modeling teaches you to identify and evaluate threats and vulnerabilities during the design phase. Learn structured methods to assess security objectives, threats, and attacks, guiding your design and security testing.
Through workshops, gain practical experience in documenting security implications and applying threat models, ensuring effective security risk mitigation in your projects.
Certificate of Competence in Zero Trust
Gain authoritative expertise in Zero Trust with the industry’s first dedicated Zero Trust security certification from the Cloud Security Alliance.
Best for OT security
OT systems are increasingly interconnected and vulnerable to cyber threats. Gain the qualifications you need to handle these threats and develop an organisations OT security.
ICS405 - Securing ICS: Becoming an Industrial Cyber Security Professional
Secure your Industrial Control Systems (ICS) with this hands-on OT security course, help prepare for the knowledge required for the challenging GICSP exam.
Gain a comprehensive understanding of IT, OT, and physical security, industry regulations, and threat mitigation strategies to protect critical infrastructure and respond effectively to cyber incidents.
Assessing and Exploiting Control Systems & IIoT
Take a deep dive into hands-on ICS/SCADA security with this cutting-edge penetration testing course—complete with lifetime updates and hardware kit, including your own PLC and RF hacking tools.
Learn to test real-world control system components using advanced pen testing techniques, RF analysis, and embedded circuit attacks, all structured around a proven methodology developed for the U.S. Department of Energy.
Gain a cyber security certification with QA
Interested in cyber security certification training with us? Book a course online or contact our team today to discuss your requirements.
We partner with world leading cyber security vendors, including EC-Council, IAPP, ISACA, ISC2, PECB and Microsoft. We have more than 25 specialist cyber instructors who, across a range of national programmes, have educated 25,000+ students in the last four years.
Explore cyber security reads

Let's talk
Start your digital transformation journey today
Contact us today via the form or give us a call


