Pictured often as someone sitting in a darkened room (wearing an even darker hoodie) there is little widespread understanding of who ethical hackers are, and what they actually do.
QA has worked with hundreds of organisations to strengthen their cyber-security capabilities, and has trained thousands of people in ethical hacking practices. Using a six-step framework, we explore how ethical hackers mimic the activities of real threats, and the questions organisations should be asking themselves to make sure they are adequately protected.
What is an Ethical Hacker?
A hacker is generally identified as someone who breaks into computer systems and networks, often for some gain. Whatever the motive (financial, political, social), a hacker generally acts outside the law in an unauthorised capacity.
The ‘hacker’ image is well-known. Working in a dimly-lit room, with an array of large, bright computer screens, breaking into any system in seconds with nothing more than a few lines of fast-typed code.
The reality is much more diverse. Hackers aren’t all young. They don’t all wear hoodies. They rarely operate in darkened rooms. And they certainly rely on more than their coding abilities to attack systems. Hacking is a diverse set of technical and people skills, not a personality.
An ethical hacker does everything a hacker does, but acting in an authorised capacity within the law. They have the same skill-set, but a better oriented moral compass.
Just like their malicious counterparts, an ethical hacker seeks out weaknesses in systems, reverse-engineers code to make it do things it was not originally designed to do, and gains access to systems designed to remain private. In so doing, they highlight weaknesses in security, and support organisations to fix vulnerabilities before cyber-criminals find and exploit them.
What does an ethical hacker do?
In our experience, good ethical hackers will spend a lot of time on personal development – researching and understanding the latest industry updates and developing new skills. The world of cyber changes hourly, with software updates for a major system being released every day. It’s a cat-and-mouse game, so to be effective, ethical hackers have to stay ‘ahead of the curve’ and keep up with all the very latest developments. They will:
- Read – technical notes, blogs, boards, forums, etc.
- Attend conferences and technical meetings with other professionals
- Attend training courses
How much time does it really take? In our experience, an ethical hacker will typically spend 2-3 hours a day reading and talking to other professionals to keep their skills up-to-date.
A six-step framework for understanding the hacking process
On the days where the hacking skills get brought into play, the hacking process follows a clear six-step framework.
Step 1: Permissions
What an ethical hacker will do:
In most circumstances, hacking is illegal. Before any ethical hacker starts work, there must be a detailed, written scope of works outlining areas on- and off- limits, and full signed legal approval to proceed. Failure to do so will put the hacker, and potentially the organisation, at risk of breaking the law. This is not ethical.
Questions organisations should ask themselves:
- Have you got an up-to-date list of which systems may be subject to attack from an ethical hacker under your instruction, and approximately when? Is a well-defined process in place to manage this?
- Have you got all the right permissions and contacts in place to identify if a breach is your ethical hacker, or a malicious breach happening at the same time? How will you know the difference?
- Do the right people (but only the right people) know that an ethical hacker has been instructed to attempt a breach on your systems?
Step 2: Reconnaissance (a.k.a Footprinting)
What an ethical hacker will do:
Hackers need to know everything about the target (even the coffee shops that staff go to). Why? Overheard conversations between employees outside the office could reveal vital information. The weakest link is rarely the IT system, it's usually the user. They will typically use four techniques: open-source intelligence, network analysis, dumpster diving, and social engineering.
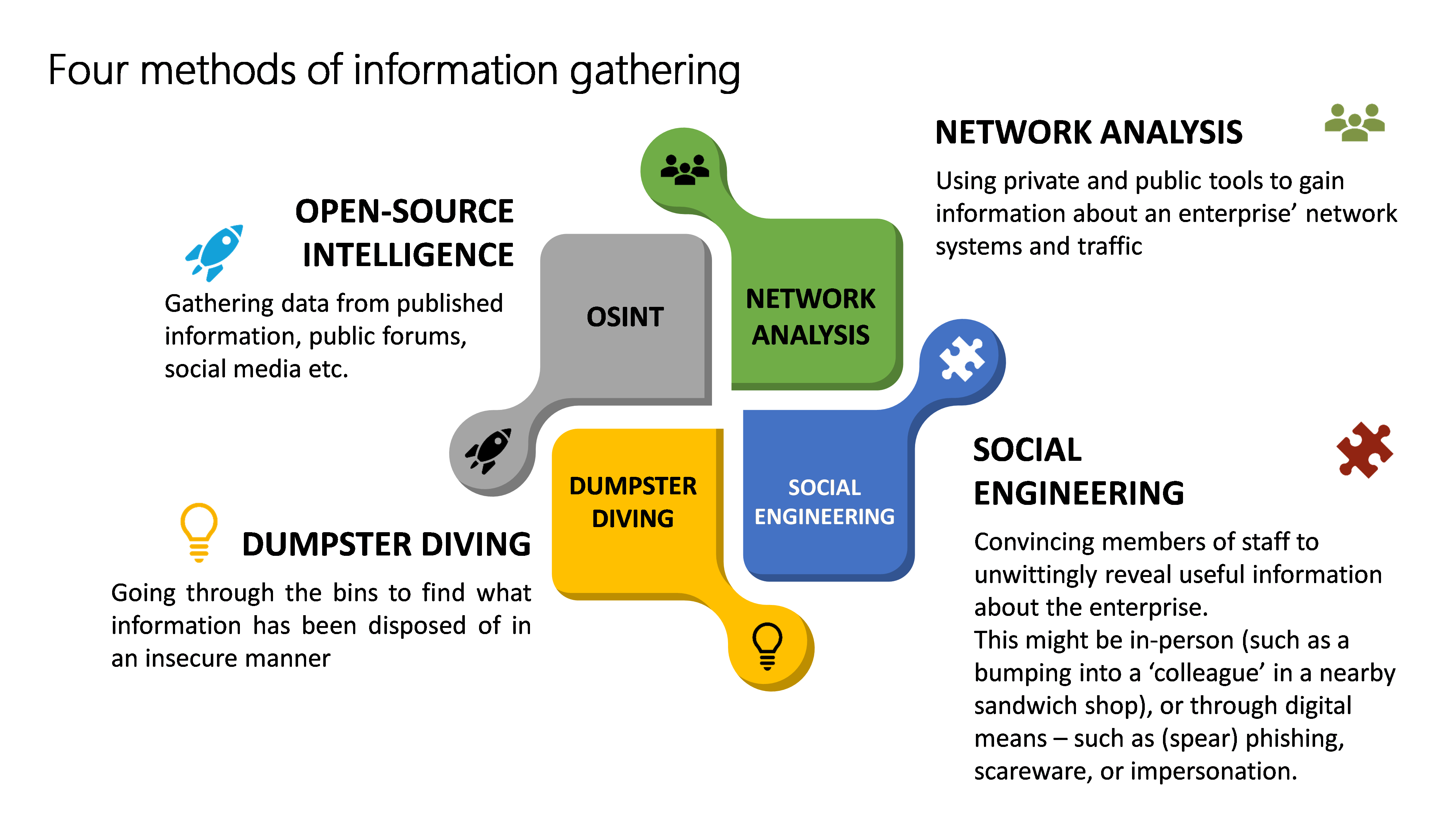
Some information is particularly valuable to hackers: emails, phone numbers, software versions, project names, supplier details, site maps – along with any information about the security measures an organisation takes to protect itself (e.g. password rules).
Questions organisations should ask themselves:
- What information has the organisation published publically that might be useful to a hacker?
- Can it be redacted?
- Does it have to be published?
- Can it be published in a different way, that’s less useful to a hacker?
- What systems and processes are in place to stop information being revealed in the open by mistake?
- Is there a clear-desk policy?
- Do employees meet and discuss work in public places?
- Do staff take documents home with them?
- Have staff been trained to spot the signs of a social-engineering attack?
- How aware are staff of the techniques that hackers may use?
- How widespread is good preventative practice?
- How easy is it for employees to report suspicious activity?
Step 3: Gaining access
What an ethical hacker will do:
This is where the hacker’s art comes to the forefront. In the films, a protagonist sits in a darkened, smoke-filled room with multiple monitor screens and a blue-LED glow from various hi-tech looking devices. The reality is very different.
Data from the reconnaissance step will be used to gain access – either remotely via the networks (using vulnerabilities in software) – or physically by entering the building. Hackers will have found the weak spots and the route with the best chance of success. It might be exploiting a complex software vulnerability, or it might be walking straight through the front door with a clipboard and a high-vis vest. In all cases, hackers will try to gain access in a way that raises little suspicion, and leaves little trace.
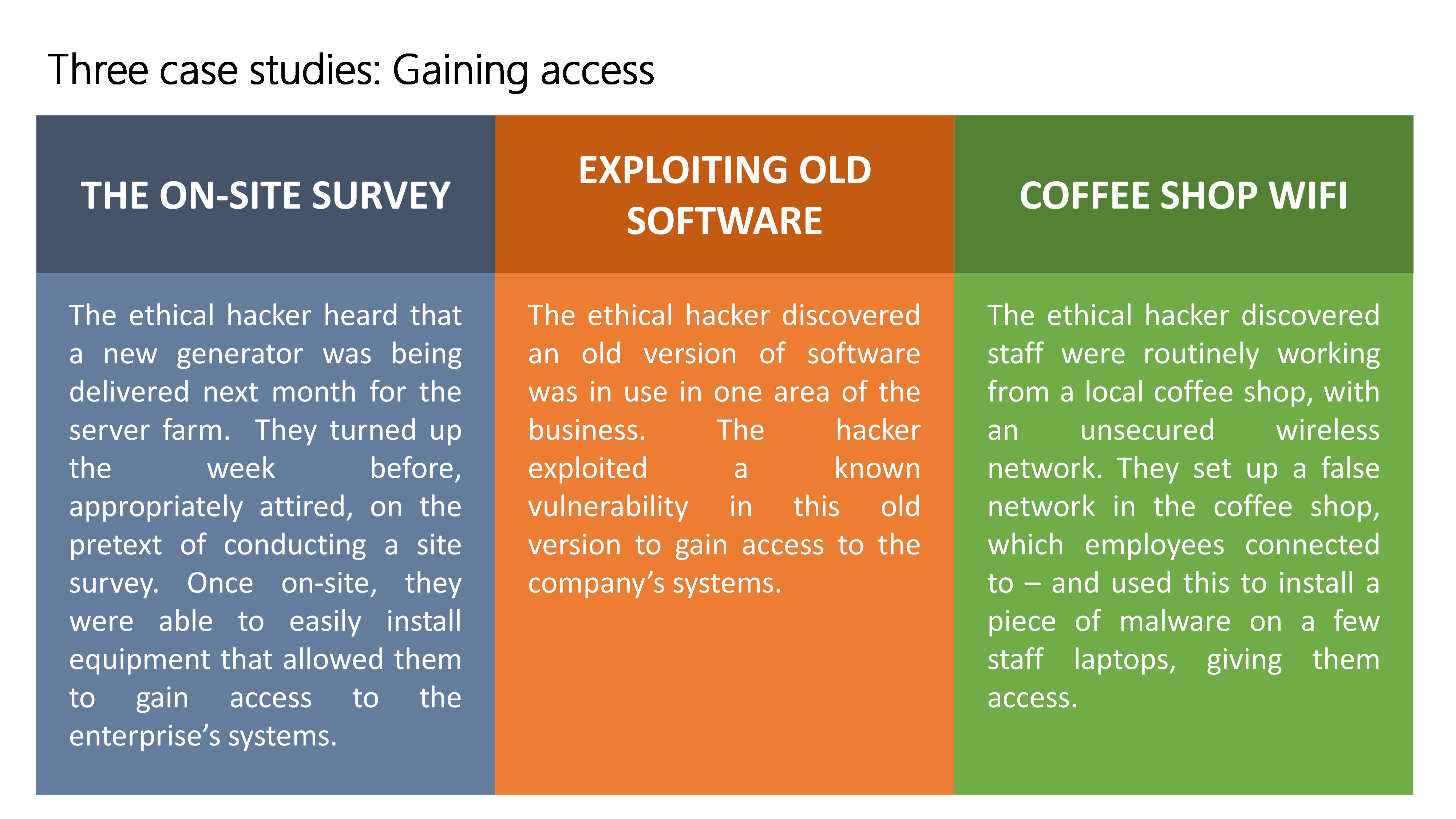
Questions organisations should ask themselves:
- How good are staff at avoiding high-risk activity that may compromise your systems? (e.g. using public WiFi)
- What hardware and software systems do you have to prevent malicious software or hardware being installed?
- What monitoring systems and processes do you have to identify when there has been a breach?
Step 4: Maintaining access
What an ethical hacker will do:
Once access has been gained, a hacker will seek to make changes to the systems that allow them to ‘go back to the scene of the crime’ – allowing them to gain access in the future. An attack is rarely a one-off hit. The hacker might plant backdoors in software, or create new user accounts.
Questions organisations should ask themselves:
- After an attack, how do you review other potential vulnerabilities?
- How robust are your processes for monitoring who has access, and when they use it?
- Do you have enough high-level cyber security professionals in your organisation to spot, and close, software vulnerabilities?
Step 5: Covering tracks
What an ethical hacker will do:
A good ethical hacker will, just like a malicious hacker, try to remove all evidence of their visit – so there’s no suspicion of a breach at all. The hacker wants two things. First, to reduce the chances of you identifying how someone gained access (or perhaps, that you’ve even been compromised at all). Second, the hacker wants to reduce the chances of being identified – if the breach is spotted and an investigation is launched. At a bare minimum this will include deleting logs, wiping audit trails and deleting user accounts, but will often go deeper – sometimes including the physical destruction and disposal of the hardware used to commit the attack.
Questions organisations should ask themselves:
- Are the right protections in place to prevent people from removing evidence of historic activity?
- Do you have access to the right expertise to identify if evidence has been erased, and to investigate at a forensic level what can be recovered?
Stage 6: Enumeration
What an ethical hacker will do:
Up to this point, the activities of a malicious and an ethical hacker have differed very little. However, unlike a normal hacker, an ethical hacker will detail each and every step they take, so that remedial works can be done to make sure the holes are fixed. It is a painstaking, yet necessary task – and is the source of much of their value.
Questions organisations should ask themselves:
- What is the feedback process for listening to, and acting upon, the findings of the ethical hacker?
- Do you have sufficient capacity and capability in your IT and cyber workforce to make changes to strengthen weaknesses identified?
So, in conclusion - why ethical hacking is the way forward
Ethical hacking can be a very powerful tool in the fight against cyber-crime. It is the ultimate (safe) way to identify weaknesses in your digital perimeter. However, the weaknesses it exposes are just as often in the organisation and its practices, as they are in hardware and software. To remain cyber-safe everyone needs to know the risks and be cyber-literate – not just the IT department.
About the author
Mark Amory is Senior Technical Trainer in QA’s Cyber Practice. He leads the development of our Cyber Security curriculum, and works with our customers on cyber security. He’s an expert in internet and World Wide Web technologies, security, malware, communications protocols, information assurance and information security. And, he’s a certified ethical hacker.
Want to up your cyber security capability?
Check out our cyber security and cyber security certification training courses, including Certified Ethical Hacker.
